This is part 4 of a series of networking posts:
OSI stands for Open Systems Interconnection and it was developed in 1974 by the International Organization of Standardization (ISO). It is a 7 layer architecture with each layer having specific functionality to perform in order to transmit data from one server to another.
What does it look like?
Image Reference: https://www.geeksforgeeks.org/layers-osi-model/
tl;dr Google Request Scenario
Part 1 (on your local laptop): When you request Google from a browser: The browser creates a GET request. The Presentation layer encodes it to HTTP/S. Session layer opens a connection from you and the server. The GET request gets put into a TCP packet. Then the Network layer figures out the next IP it needs to send it to, in this case your router. The Data link (my computer's Network Interface Card = NIC) converts it to electrical signals. The Physical layer transmits the TCP packet over the air from my computer to the router over WiFi (or to your router via a physical wire if you set that up).
Part 2 (on your router):When the router receives the TCP packet, it's over the WiFi Physical layer (most routers today have WiFi built it, however it used to be a separate box). Then it has to translate this Physical layer from electrical signals (Physical) into bits (Network) with the router's NIC. Then the Network layer (router) figures out based on the destination IP address where to send it to next. It transfers the data back into electrical signals and sends it out the physical cable to your cable company and onwards.
Long Explanation of Scenario and Layers:
There are apps an end-user can utilize that will work at the Application layer. As an end-user you only see the interface Edge. The app itself, such as Edge, can utilize for example .NET Framework's HttpClient in order to work with the networking Application layer. (other browsers and things have other development frameworks that can work with the Application layer).
I want to access https://www.google.com from Edge so this sends a GET request. All GET/PUT/POST/PATCH/DELETE requests are at the Application layer and are HTTP protocols.
You need to download the HTML for the page google.com, so Edge opens a Session and requests and start downloading the HTML page in chunks.
Presentation layer converts chunks of data from a network format to an application format, and vice versa. The Presentation layer takes care of encryption/decryption of the file, and combining chunks of the file as it comes through.
There are multiple cycles of going through the software layers.
The Transport layer is a connection between two servers, so in this case, your computer to Google's servers. Transport layer protocols are Transmission Control Protocol (TCP), User Datagram Protocol (UDP). TCP provides apps a way to deliver (and receive) an ordered and error-checked stream of information packets over the network. TCP is slower due to its error checking and needed if you want to ensure things (like files) are delivered without issues/errors. The User Datagram Protocol (UDP) is used by apps to deliver a faster stream of information by doing away with error-checking. This is used more often for video streaming or gaming where you need faster speed/performance and can handle a little bit of errors.
The Network layer is IP and handles routing packet. A packet is a chunk of data. It will route data based on logical addressing. Routers are part of the Network layer because when you send something, there are multiple hops it must make, so the network layer handles determining which path the data should take (which hops to do) based on network conditions, service priority, and more. if there are traffic issues it can also handle switching and re-routing packets.
The Data Link layer will translate the Physical to the Network layer (Network layer = electrical representation of data like bit patterns, encoding, and tokens). The Network Interface Card (NIC) works at this layer.
The Physical Layer is entirely hardware over a physical medium and connects computers via a physical link. It defines how a cable can attach to a Network Interface Card (NIC) by determining the number of pins a connector will have and the functionality. This can either be wired or wireless (Wi-Fi).
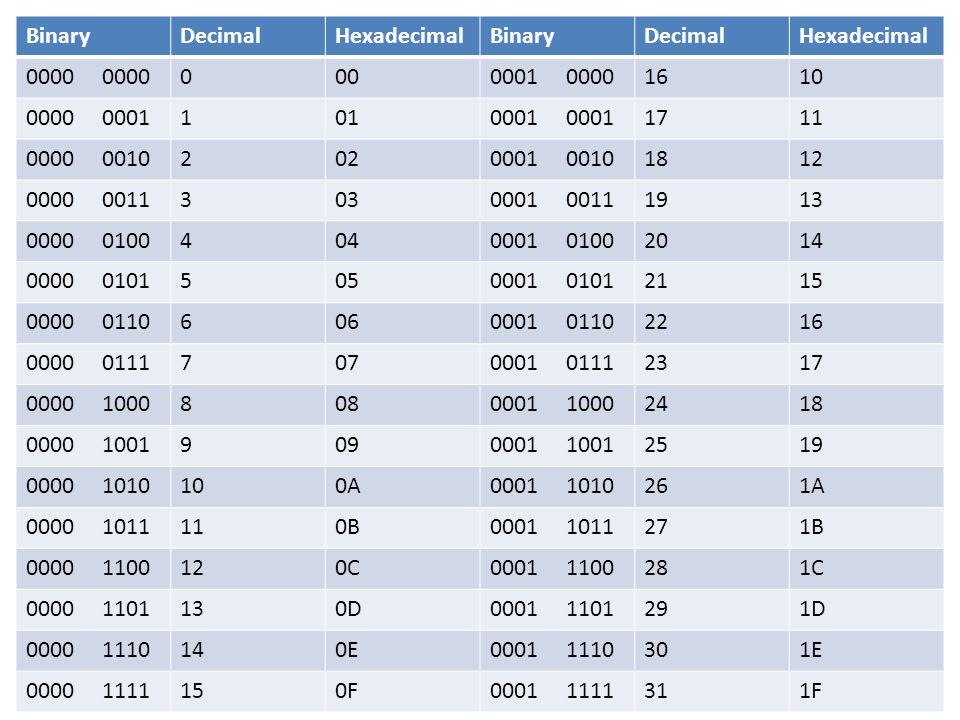
- Part 1: Binary
- Part 2: Hexadecimal
- Part 3: Networking 101 (IP addresses, subnets, etc.)
- Part 4: Scenario based understanding of the 7 layers of the OSI Model
- Part 5: Azure Networking Foundations - VNet, Subnet, Security, and Connectivity
- Part 6: Azure Networking - VMs, IP Addresses, and Load Balancing
OSI stands for Open Systems Interconnection and it was developed in 1974 by the International Organization of Standardization (ISO). It is a 7 layer architecture with each layer having specific functionality to perform in order to transmit data from one server to another.
What does it look like?
Image Reference: https://www.geeksforgeeks.org/layers-osi-model/
tl;dr Google Request Scenario
Part 1 (on your local laptop): When you request Google from a browser: The browser creates a GET request. The Presentation layer encodes it to HTTP/S. Session layer opens a connection from you and the server. The GET request gets put into a TCP packet. Then the Network layer figures out the next IP it needs to send it to, in this case your router. The Data link (my computer's Network Interface Card = NIC) converts it to electrical signals. The Physical layer transmits the TCP packet over the air from my computer to the router over WiFi (or to your router via a physical wire if you set that up).
Part 2 (on your router):When the router receives the TCP packet, it's over the WiFi Physical layer (most routers today have WiFi built it, however it used to be a separate box). Then it has to translate this Physical layer from electrical signals (Physical) into bits (Network) with the router's NIC. Then the Network layer (router) figures out based on the destination IP address where to send it to next. It transfers the data back into electrical signals and sends it out the physical cable to your cable company and onwards.
Long Explanation of Scenario and Layers:
There are apps an end-user can utilize that will work at the Application layer. As an end-user you only see the interface Edge. The app itself, such as Edge, can utilize for example .NET Framework's HttpClient in order to work with the networking Application layer. (other browsers and things have other development frameworks that can work with the Application layer).
I want to access https://www.google.com from Edge so this sends a GET request. All GET/PUT/POST/PATCH/DELETE requests are at the Application layer and are HTTP protocols.
You need to download the HTML for the page google.com, so Edge opens a Session and requests and start downloading the HTML page in chunks.
Presentation layer converts chunks of data from a network format to an application format, and vice versa. The Presentation layer takes care of encryption/decryption of the file, and combining chunks of the file as it comes through.
There are multiple cycles of going through the software layers.
The Transport layer is a connection between two servers, so in this case, your computer to Google's servers. Transport layer protocols are Transmission Control Protocol (TCP), User Datagram Protocol (UDP). TCP provides apps a way to deliver (and receive) an ordered and error-checked stream of information packets over the network. TCP is slower due to its error checking and needed if you want to ensure things (like files) are delivered without issues/errors. The User Datagram Protocol (UDP) is used by apps to deliver a faster stream of information by doing away with error-checking. This is used more often for video streaming or gaming where you need faster speed/performance and can handle a little bit of errors.
The Network layer is IP and handles routing packet. A packet is a chunk of data. It will route data based on logical addressing. Routers are part of the Network layer because when you send something, there are multiple hops it must make, so the network layer handles determining which path the data should take (which hops to do) based on network conditions, service priority, and more. if there are traffic issues it can also handle switching and re-routing packets.
The Data Link layer will translate the Physical to the Network layer (Network layer = electrical representation of data like bit patterns, encoding, and tokens). The Network Interface Card (NIC) works at this layer.
The Physical Layer is entirely hardware over a physical medium and connects computers via a physical link. It defines how a cable can attach to a Network Interface Card (NIC) by determining the number of pins a connector will have and the functionality. This can either be wired or wireless (Wi-Fi).